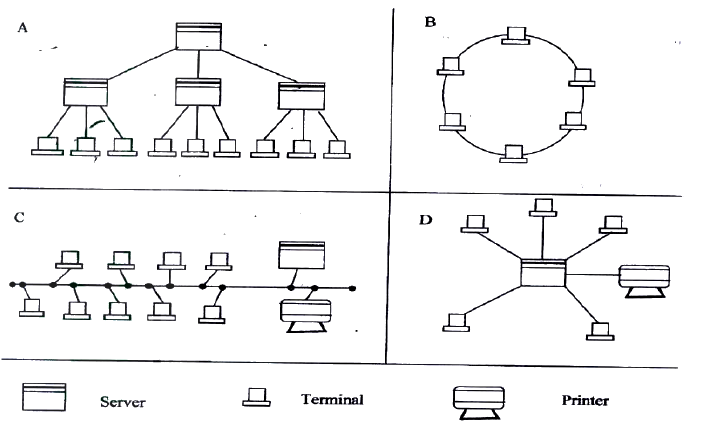
The diagram below shows four common network topologies A, B, C and D.
i) Name the network topologies labeled a, B, C and D.
ii) Explain what happens if server X in topology A fails. iii) List two problems associated with network topology B. iv) List two disadvantages associated with network topology D. b) Differentiate between Interment and World Wide Web: c) Describe the following network services and identify their applications. i) Voice mail ii) Video conferencing
ANSWERS
i) Name the network topologies labeled A, B, C and A Tree/Hierarchy B Ring C Bus/Multi drop D Star ii) Explain what happens if server X in topology A fails. The terminal connected to X will be affected/stop communicating with the ret of the network iii) List two problems associated with network topology B. Difficult to trouble shoot "- Failure of one terminal results in network breakdown Extra cost of extra NIC card. iv) List two disadvantages associated with network topology D. Failure of central device/server results I total collapse of network Extra cost of cabling as each terminal must be cabled separately to the hub. b) Differentiate between Internet and World Wide Web. The Internet is a massive network of networks, a networking infrastructure. It connects millions of computers together globally, forming a network in which any computer can communicate with any other computer as long as they are both connected to the Internet. Information that travels over the Internet does so via a variety of languages known as protocols. The World Wide Web, or simply Web, is a way of accessing information over the medium of the Internet It is an information-sharing model that is built on top of the Internet The Web uses the HTTP protocol, only one of the languages spoken over the Internet, to transmit data. Web services, which use IfTTP to allow applications to communicate in order to exchange business logic, use the Web to share information. The Web also utilizes browsers, such as Internet Explorer or Netscape, to access Web documents called Web pages that are linked to each other via hyperlinks. Web documents also contain graphics, sounds, text and video. c) Describe the following network services and identify their applications. i) Voice mail Voicemail (or voice matt, voicemail or VMS, sometimes called message bank) is a centralized system of managing telephone messages for a large group of people. In its simplest form it mimics the functions of an answering machine, uses a standard telephone handset for the user interface, and uses a centralized, computerized system rather than equipment at the individual telephone. Voicemail systems are much more sophisticated than answering machines in that they can: Answer many phones at the same time Store incoming voice messages in personalized mailboxes associated with the user's phone number Enable users to forward received messages to another voice mailbox send messages to one or more other user voice mailboxes Add a voice introduction to a forwarded message Store voice messages for future delivery Make calls to a telephone or paging service to notify the user a message has arrived in his/her mailbox Transfer callers to another phone number for personal assistance Play different message greetings to different callers. ii) Video conferencing. A videoconference (also known as a video teleconference) is a set of interactive telecommunication technologies which allow two or more locations to interact via two-way video and audio transmissions simultaneously. It has also been called visual collaboration and is a type of groupware.
0 Comments
Distinguish between the following sets of terms as used in spreadsheets. Worksheet and workbook, Filtering and sorting
b) A student’ database comprises of students’ details table and fees received table as shown below:
Students’ details table
i) State the primary key field for each table.
ii) State the field, which should serve as the linking field for the two tables. c) Describe the following terms with respect to computer security: i) Logic bombs ii) Physical security iii) Tapping d) List three functions of antivirus software.
(i) Log files
(i)State the primary key field for each table.
c) Describe the following terms with respect to computer security: i)Logic bombs A computer virus that is activated after a series of event/commands/date ii) Physical security Threats that threaten the physical nature of computer equipment e.g. Fire, Lightening water, building access etc iii) Tapping.
Distinguish between the following sets of terms as used in spreadsheets. Worksheet and workbook, Filtering and sorting
b) State one way in which a user may reverse the last action taken in a spreadsheet package.
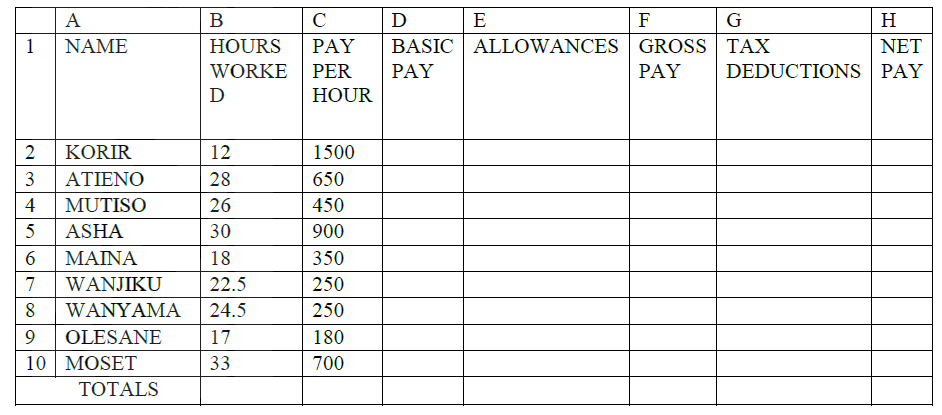
c) The following is a sample of a payroll. The worksheet row and column headings are marked 1, 2, 3, . and A, B, C. respectively
Use the following expressions to answer the questions that follow:
i) D2 ii) E4 iii) F10 iv) G7 v) H5 d) i) State three ways of moving round the page in a Desktop Publishing window. ii) State two ways on how information & Communication Technology (ICT) can be used to reduce the spread of HIV/AIDS
EXPECTED RESPONSES
(a) Distinguish between the following sets of terms as used in spreadsheets
(i) Worksheet and workbook
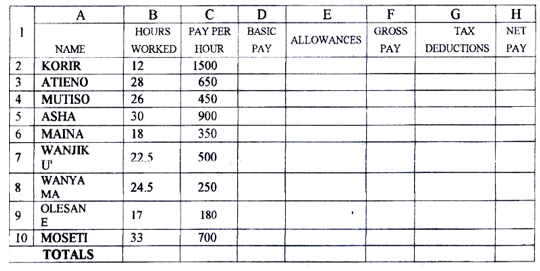
Use the undo command (ctrl + z) (c)The following is a sample of a payroll. The worksheet row and column headings are marked 1, 2, 3, and A, B, C respectively
Use the following expressions to answer the questions that follow
List two examples of:Third generation languages and Object oriented languages
b) List and explain three types of user interfaces.
c) Describe the following categories of software: i) Firmware ii) Proprietary software d) a new company XYZ intends to go into the business of desktop publishing. Advise the company on three computer hardware system specification features to consider as a measure of enhancing performance.
(a) One of the functions of an operating system is job scheduling.
Explain what is meant by job- scheduling Running of a particular job/ task under a system of priority, computer resource availability, time allocated to user etc. (b) List and explain three types of user interfaces
List two examples of:Third generation languages and Object oriented languages
i) Third generation languages
ii) Object oriented languages b) Draw a flowchart to compare three non-equal numeric values A, B, C and prints the largest of the three.
(a) List two examples of:
(i) Third generation languages Pascal, basic, c (ii)Object oriented languages VB, Small talk, C++ The diagram below shows a formatted plate surface of a storage disk.
Shade and label:
a) one sector b) One block List two methods of gathering information during system development process.
Distinguish between margins and borders as used in word processing
List two arithmetic operations that can be performed on a row of numeric data in a word processing table.In each case of (a) above, write the expression used.Explain the following graphic terms: Rotate and Crop
State two application areas of a desktop publishing software.
Explain the following software terms: Portability and Modularity
(a)Portability
Ability of a software to work/ function in several computer hardware and O/S platforms (b)Modularity Ability of software to be broken down into several sections for easier understanding and maintenance. Explain two ways in which ICT can enhance commerce.
Differentiate between COM ports and LPT ports
What is an Internet Service Provider?
b) An employee in a business company is charged with the responsibility of putting the company advertisements on the Internet.
ANSWERS
(a) What is an internet service provider?
A company that provides internet services. Connects users to the internet (b) An employee in a business company is charged with the responsibility of putting the company advertisement on the internet (i) State the professional title of the employee Web administrator, web designer (ii) Give an example of software used by this employee to carry out the above task HTML, Dream weaver, MS Front Page What actions should be taken in case of a fire outbreak in the computer laboratory?
What meant by the term user-friendly as used in software development?
what are peripheral devices?
Give two examples of peripheral devices
Distinguish between transcription and transposition types of errors and give an example of each22/12/2020 Distinguish between transcription and transposition types of errors and give an example of each
What is meant by; Analogue data and Digital data
(a) Analogue data: Data that is based on physical variations such as loudness and pitch, electoral voltages
(b) Digital Data- Data, which use the computer’s binary number systems 0 and 1 |
Categories
All
Archives
December 2024
|
Can't find what you are looking for? Don't worry, Use the Search Box Below.
|
Primary Resources
College Resources
|
Secondary Resources
|
Contact Us
Manyam Franchise
P.O Box 1189 - 40200 Kisii Tel: 0728 450 424 Tel: 0738 619 279 E-mail - sales@manyamfranchise.com |


















 RSS Feed
RSS Feed

