A head teacher keeps the following student details in a database: Name,address, Town, Date of Birth, Marks scored, Fees paid.
i) Name the most appropriate primary key. Give a reason
ii) For each item in the student’s details above, indicate its most appropriate data type as used in the database. iii) Explain why input screens are better data entry designs than entering data directly to a table. b) List two career opportunities associated with databases. c) Distinguish between: i) A table in word-processing application and a table in a database application ii) Mouse pointer and insertion point. d) Outline the steps to be followed in order to merge cells in a word processing table.
RESPONSES
i)Name the most appropriate primary key. Give a reason. Name alone is not unique though it is very rare that two or more students will share the same name. ii)For each item in the student's details above, indicate its most appropriate data type as used in the database.
0 Comments
A manager wishes to replace the current manual system with a computerized one
a) Describe three main areas that must be evaluated to justify the replacement
b) List the three areas that would be considered in the requirements specifications. c) State and explain three ways that can be followed to replace the current system
A manager wishes to replace the ctirrent manual system with a computerized one
a) Describe three main areas that must be .evaluated to justify the replacement.
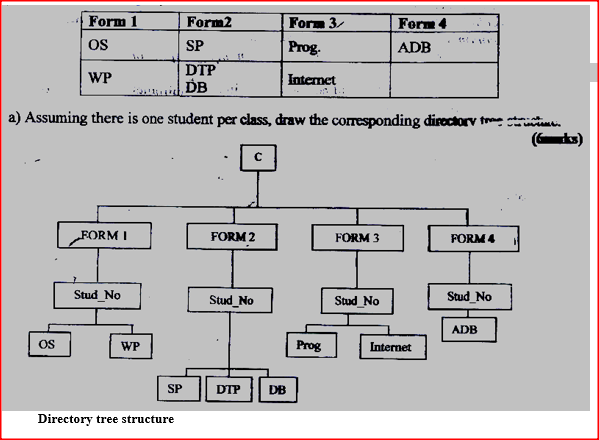
A computer C directory has folders for form 1, form 2, Form 3 and form 4. Each class has student’s folders labeled according to their number. The students create their own folder for the subject the are studying based on the table shown below
a) Assuming there is one student per class, draw the corresponding directory tree structure.
b) i) a form four student wants to create a folder to store her project. State the path for that project folder. ii) Suggest how the student can ensure that: 1. Work is not lost in case the hard disk fails. 2. The project is not copied by other students. c) i). Other than I/O devices, list other three devices under the control of the operating system. ii) Explain any one of the devices named in C (i) above d) Define the term trouble shooting
RESPONSES
c) i) A form four student wants to create a folder to store to project State the path for flat project folder.
C:\FORM4\STUDNO\ADB\PROJECT ii) Suggest how the student can ensure that: - work is not lost in case the hard disk fails.
e) Define the term trouble shooting
Define the following web related terms: Web browser, Hyperlink ,Hypertext document
Define the following web related terms: Web browser, Hyperlink ,Hypertext document
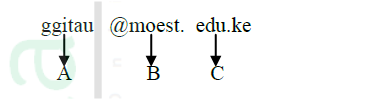
i) Web browser ii) Hyperlink iii) Hypertext document b) List six activities performed on the web c) An institution has ten stand alone computers i) Suggest with reasons the most appropriate topology required to inter-connect the computers. ii) State the necessary steps required to connect the computers to the internet. d) Below is an email address: Name the parts labeled:
a) Define the following web related terms:
i) Web browser A browser is an application program that provides a way to look at and interact with all the information on the World Wide Web. ii)Hyperlink This is the clickable link in text or graphics on a Web page that takes you to another place on the same page, another page, or whole other site. iii) Hypertext document A document usually web document (file) where the user interacts with the whole document using hyperlinks b) List six activities performed on the web
i) Suggest with reasons the most appropriate topology required to inter-connect the computers. a) Bus Reason: Easy to set up, Low cost in terms of cabling QR b)Star Reason: Speed of data transmission is high, Easy to troubleshoot via central hub or switch ii) State the necessary steps required to connect the computers to the Internet.
ggitau @moest. edu.ke Name the parts labeled:
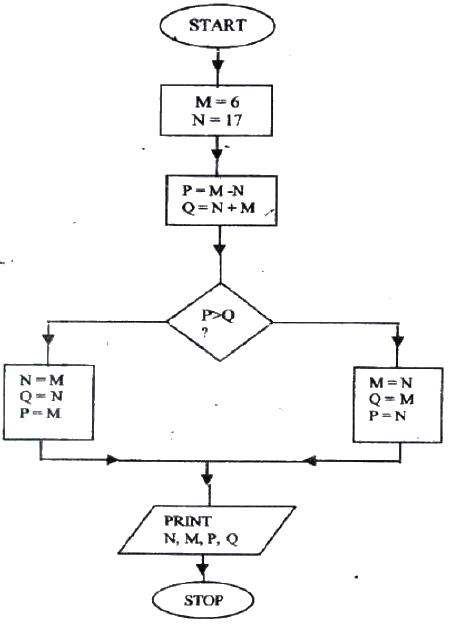
Study the flowchart below and answer the questions that follow
i) Name the control structures used in the flowchart
ii) Determine the values of M, N, P and Q. M………………………….. N……………………….. P ………………………….. Q ……………………… iii) Write the pseudo code for the flowchart b) List four functions of an assembler
ANSWERS
i) Name the control structures used in the flowchart.
- Selection -Sequencing ii) Determine the values of M, N, P and Q. M………17………………..N……………….17………………….. P………..17………………..Q……………….17…………………. iii) Write the pseudo code for the flowchart Q=N
a) Translate assembly language to machine code. b) Execute assembly language statements. c) Create executable files (.exe) from the assembly language statements. d) Allocate memory for machine code. e) Debug for errors Write an algorithm to compute the area of a triangle.
List four factors to be considered when purchasing an operating system.
Differentiate between the following pair of terms as used in database design:Input mask and design and Table and query
a)Input mask and design
An input mask often refers to a string expression that a developer defines which governs what is allowed to be entered into a typical edit/input box. b) Table and query Table - the basic unit of storing data in database Query - a view created from table(s) that returns specific records based on a criterion. List four types of publications that can be designed by using desktop publishing software.29/12/2020 List four types of publications that can be designed by using desktop publishing software.
State the function of each of the following: Network interface card, Network protocol and Hub29/12/2020 State the function of each of the following:Network interface card, Network protocol and Hub
a) Network interface card
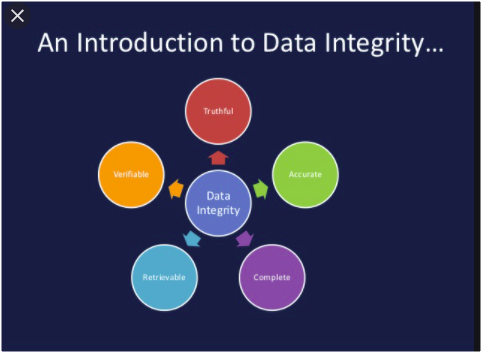
Describe the term data integrity and State four situations in which data may lose integrity.29/12/2020 Describe the term data integrity and State four situations in which data may lose integrity.
a) Describe the term data integrity.
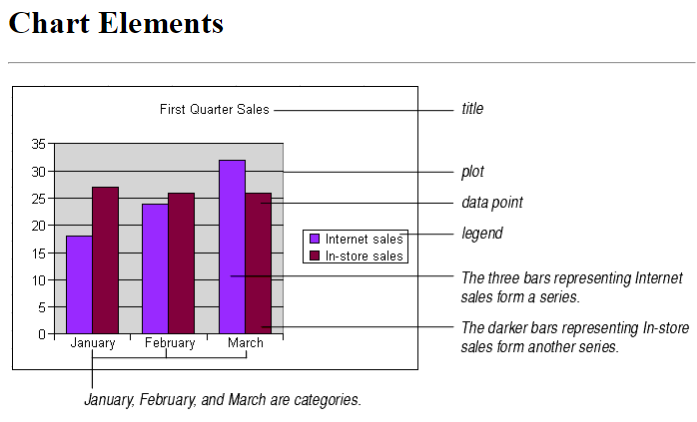
Explain data series, axis and legends as used in spreadsheet charts. Data, Axis and Legend29/12/2020 Explain data series, axis and legends as used in spreadsheet charts. Data, Axis and Legend
Data Series
State four benefits of using a computer in a school library
You have been asked to change your computer password. State a precaution you need to take in order to avoid each of the following: a) Forgetting the password
b) Hacking
Some of the storage disk available are: zip disks, 3 ½ inch floppy disks, DVDs and 5 ¼ inch floppy disks. Arrange these devices in ascending order of storage capacity.
List four ways of acquiring software in an organization
Define authenticity as used in software selection
Jane has noticed the following problems in her computer keyboard
a) Disk is fragmented - Defragment the disk by running the defragment utility. "
b) Virus/bug infection - run the antivirus utility c) Capacity of RAM is small- Increase the size by replacing the existing chip with a higher capacity RAM chip. d) Processor speed is low - Replace processor with a high speed processor. State the functions of the following keys on the computer keyboard; Backspace and Insert (ins)29/12/2020 State the functions of the following keys on the computer keyboard; Backspace and Insert (ins)
Describe the computer booting process.
|
Categories
All
Archives
December 2024
|
Can't find what you are looking for? Don't worry, Use the Search Box Below.
|
Primary Resources
College Resources
|
Secondary Resources
|
Contact Us
Manyam Franchise
P.O Box 1189 - 40200 Kisii Tel: 0728 450 424 Tel: 0738 619 279 E-mail - sales@manyamfranchise.com |















 RSS Feed
RSS Feed

