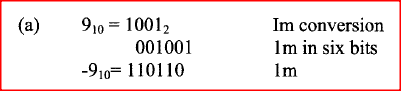
Using ones complement, convert the decimal number -9 into a 6-bit binary number.
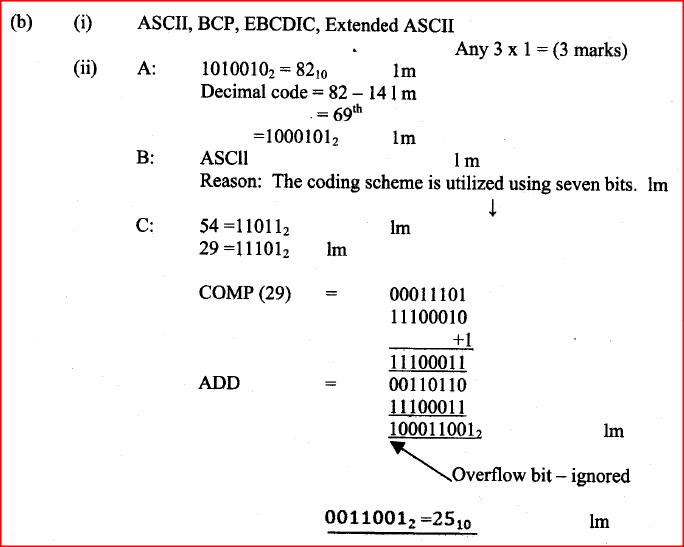
(b) (i) State three standard coding schemes used in data representation.
(ii) In a certain coding scheme, each character occupies 7 bits. Letters of the alphabet are assigned consecutive codes. If letter N is represented by 1010010. What is the representation of letter A in this coding scheme? (c) Using twos complement. show how the arithmetic below would be carried out on a 8-bit computer system. (+54)- (+29)
0 Comments
Explain how data in a computer system is secured using:
(i) password;
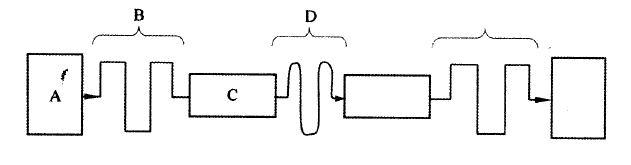
(ii) user access level. (b) State three characteristics of a suitable password. (c) State two characteristics of a computer that is infected by computer viruses. (d)(i) The figure below shows how data is transmitted through a public telephone line.
Name A, B, C and D.
(ii) State two advantages of using fibre optic cables over satellite in data communication.
(a) (i) Password
Using two examples, explain the term field properties as used in database design.
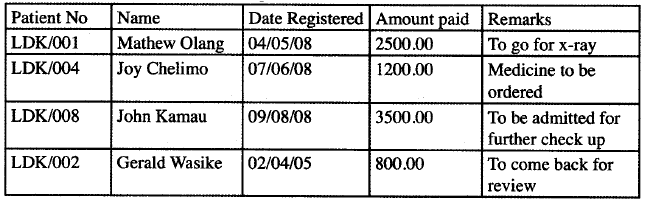
(b) Below is an extract from a hospital database table.
(i) State with reasons the most suitable data types for the following fields:
(iii) What is the purpose of a primary key field in database design? (iv) Describe how information about patients who registered after 09/08/06 can be extracted from the database.
(a)Field property:
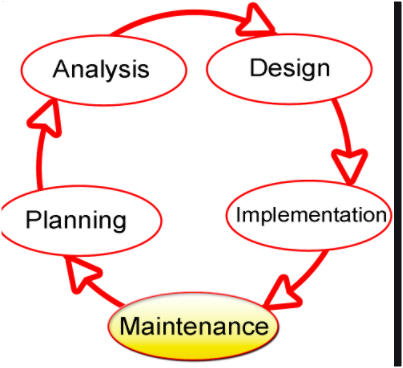
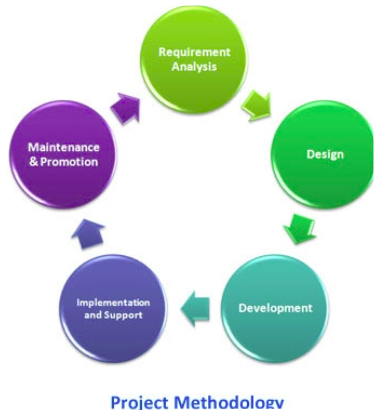
The following are some of the phases in the systems development life cycle (SDLC): system analysis, system design, system implementation, system review and maintenance. State four activities that are carried out during the system implementation phase.
(b) Give three reasons why system maintenance phase is necessary in SDLC.
(c) State two instances where observation is not a viable method of gathering information during system analysis stage. (d) Various considerations should be made during input design and output design.
State two considerations for each case.
RESPONSES
(a)(i) Activities (system implementation)
Machine language programs are more difficult to write than high-level language programs. State two reasons for this.
(b) In order to process examination results of students in a school, their names, index numbers and scores in 11 subjects are required. The average score for each student is then determined and a grade assigned. This process is repeated for all 40 students in a class,
Draw a flowchart to: . Read a student’s name, index number and the scores in all the subjects. . Determine the student’s average score. ‘ Assign a grade to the student depending on the average score as follows:
• Repeat the above steps for all the students in the class. (e) Below ¡s a list of program segments in different generations of programming languages. Identify the language for each.
(a) Disadvantages of machine level language It is time consuming to develop
A firm operates an order system that coordinates orders, raw materials and inventory across its three factories. Currently the orders are processed manually at each factory and communicated to the others over the phone. The management intends to computerise their operations. State the first two computer professionals who will be required and their roles.
System analyst roles
Network Engineer roles:
State three ways in which ICT can be used in shipping control.
Describe the following terms as used in mail merging: main document; and data source.(a) main document;
(b) data source.
State two reasons why it is necessary to use standard furniture in a computer laboratory.
Copyright laws are laws granting authors the exclusive privilege to produce, distribute, perform or display their creative works. It is a legal framework for protecting the works such as book publishing, motion-picture production and recording. State two challenges that are posed to these laws by ICT’.
Explain why telecommuting is not suitable for a doctor when carrying out an operation on a patient.3/1/2021 Explain why telecommuting is not suitable for a doctor when carrying out an operation on a patient.
State the purpose of each of the following memories in a computer system. RAM and Hard disk3/1/2021 State the purpose of each of the following memories in a computer system. RAM and Hard disk
(a) RAM
Holds data that is urgently need by the processor, Random-access memory is a form of computer memory that can be read and changed in any order, typically used to store working data and machine code. (b) Hard disk Used to hold large volumes of data that is not urgently required by the processor — also for back up of OS and data. Give two reasons why the use of finger prints and voice input can be used as reliable forms of security in computer systems.
They cannot be:
Study the pseudocode below and determine its output.
1. (a) T = O
(b) M = O (c) K = I 2. (a) M M±T (b) T = T+5 (c) K = K+1 3. Repeat step 2 while K < 3 4. Write M,T 5. Exit The word race is appearing several times in a long story document composed using a DTP package. How would this word be safely replaced with the word content?.
State four functions which are specific to Network Operating Systems.
Distinguish between a formula and a function as used in spreadsheets.Explain why an intranet is a more secure way to share files within an organisation compared to the internet.
Define data communication.
(b) State two characteristics of an effective data communication system.
Characteristics of an effective data communication system
List four activities carried out by a data processing system.
|
Categories
All
Archives
December 2024
|
Can't find what you are looking for? Don't worry, Use the Search Box Below.
|
Primary Resources
College Resources
|
Secondary Resources
|
Contact Us
Manyam Franchise
P.O Box 1189 - 40200 Kisii Tel: 0728 450 424 Tel: 0738 619 279 E-mail - sales@manyamfranchise.com |


















 RSS Feed
RSS Feed

