Describe the following types of relationships as used in Database design:One-to-one and One-to-many.(a) One-to-one;
(b) One-to-many.
0 Comments
Explain three reasons why an organization may need to change to a new computerised system.
(b) State why each of the following is important in system documentation.
(i) Identify the types of computer files named above. (ii) Give a characteristic of data held in each file. (iii) Name the field that should be used to link the two files.
(a) Current system may be experiencing problems thereby being unable to meet organisation requirements.
New directives may be received from authorities and the organisation must comply. Changes in the operating environment forces the organisation to change in order to fit and continue in business. e.g. competition. Changes in technology requiring the upgrading or total change in the existing system. Peer pressure need to remain fashion (b) (i) Sample data should be provided so that all modules can be tested. (ii) Output reports show that the system actually works/testing process/expected output.. (c) (i) Manual: Manual files stored in cabinets/books/paper/in-tray/out-tray. (ii) Electronic: Secondary storage devices/individual storage devices e.g. Flash. (d) (i) Student: Master file/Parent/Reference File/Primary. Register: Transaction file/Child table/Secondary. (ii) Master file: Data is static/Permanent/Semi-permanent. Transaction file: Data is dynamic/Temporary/Changes frequently (iii) Key field: Student number/Admission No/Reg. No/File No. What is meant by each of the following terms as used in the Internet?,surf, uploading and inbox.4/1/2021 What is meant by each of the following terms as used in the Internet?,surf,uploading and inbox.
(b) A school has set up its network using wireless technology to link computers. State three problems that the school is likely to experience when using this technology.
(c) List three ways by which parents can protect their children from accessing inappropriate content from the internet. (d) Explain three problems associated with using e-mail technology for communication.
(a) Surfing: Its the process of accessing /browsing/visiting internet resources like webpages.
What is meant by each of the following terms as used in table creation?
(a) What is meant by each of the following terms as used in table creation?
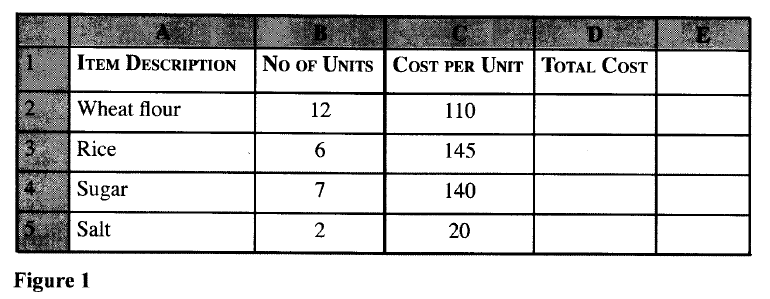
(i) cell margin; (ii) nested table. (b) State four types of text wrap that can be applied to a graphic. (c) Distinguish between each of the following: (i) axis labels and data labels; (ii) cropping and sizing. (d) Figure 1 shows a section of a worksheet containing information on household items. Use it to answer the questions that follow.
(i) Write a formula to calculate the total cost of rice.
(ii) The prices of all items increased by 10% and the value 10% is placed in cell B8. Using cell addresses with absolute referencing only, write a formula to calculate the new unit price of salt. (iii) Write a function to display the number of cells in which the cost per unit is equal to 110. (iv) Write a function to display the least total cost for all items.
(a) (i) Cell margin: Its the space between the boundary of the cell and the text/content inside the cell.
(ii) Nested table: is a table created inside another table. (b) In line with text.
State three standard data coding schemes used in computing and electronic systems.
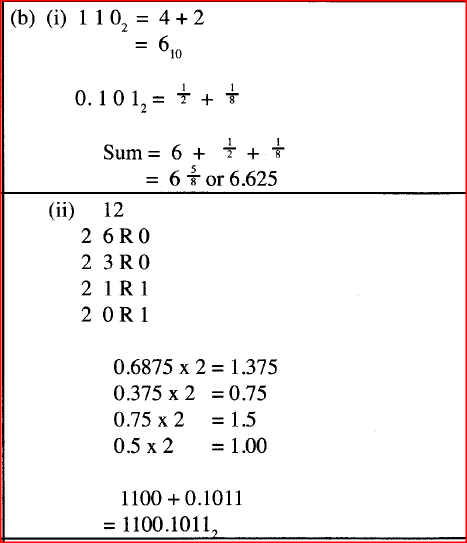
(b) Convert each of the following numbers:
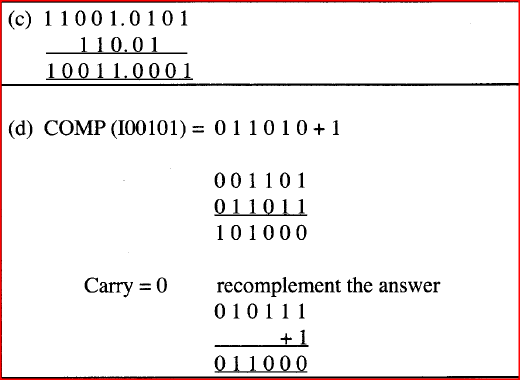
(i) 110.1012 to decimal; (ii) 12.687510 to binary; (c) Subtract 110.012 from 11001.01012 (d) Using twos complement, perform the following binary arithmetic leaving the answer in binary notation. 11012- 1001012
(a) Binary coded Decimal (BCD) )(4 bits).
Give two characteristics of scripting languages.
(b) Describe two types of errors that may be detected during program testing.
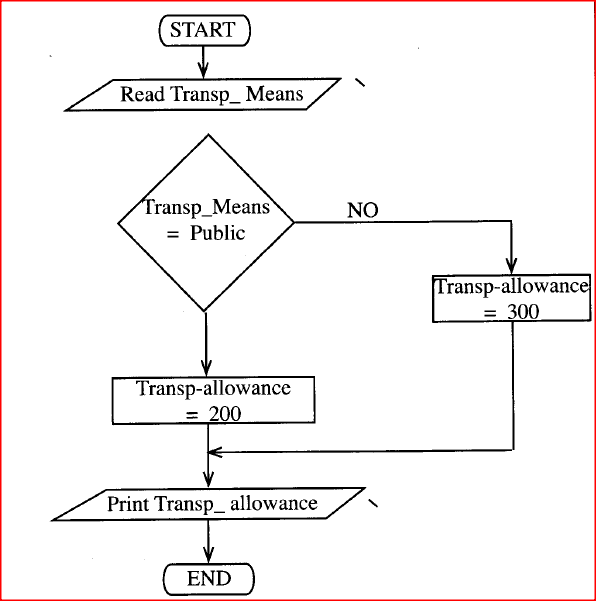
(c) A company’s workers travel to work either by public or by private means. All workers are paid a travel allowance of Ksh. 200, but those using private means are paid an additional Ksh. 100. (i) Write a pseudocode to determine a worker’s travel allowance. (ii) Draw a flowchart to determine a worker’s travel allowance. (iii) Other than occupying large space, state two disadvantages of using a flowchart instead of a pseudocode.
(a) Characteristic of scripting language:
State two application areas of real time systems.
State the importance of considering the following factors when acquiring a software; warranty;and portability.
(a) Warranty: If a software has a problem then it can be replaced.
If not working can be returned for repair. (b) Portability: To ascertain the compatibility with other systems. State the purpose of each of the following in database design.(a) input mask
(b) default value
Pesa Mingi company has offices in Nairobi and Kampala connected in a network. The management is convinced that someone is illegally gaining access to the data in their computers. State three ways in which the company can overcome this problem.
A school has acquired a system that imitates human teachers. Students can learn by getting answers from the system which they would normally get from the teacher. Give three advantages of this system.
Advantages:
A water company sends out clerks to read water meters. The data collected by the clerks is then fed into the computer and then all the bills are printed at the same time.(a) State two advantages of this approach.
Advantages:
(b) Name this type of data processing.
Identify three hardware considerations to be made before installing an operating system.
State two measures that can be put in place to control piracy of software.
A secretary saved a document in a computer. After some time, she could not remember the name and the location of the file. State four file details that are assigned a file by the operating system which can assist in tracing the file.Give two causes of such response.
A secretary saved a document in a computer. After some time, she could not remember the name and the location of the file. State four file details that are assigned a file by the operating system which can assist in tracing the file.
The accounts department of a secondary school is using a system that generates invoices that are printed in triplicate using carbon papers.(a) Name one type of printer suitable for this task.
(b) Give a reason for your answer in (a) above
Asha has a hardware shop and lately, she is finding the task of managing daily sales in the shop overwhelming.(a) State a retail system that she should acquire.
(b) State two input devices that are used in retail systems.
(c) Apart from enhancing the speed of operation, state two other benefits that Asha will gain from using such a system.
Give three reasons why primary storage devices are not used for secondary storage.
State four characteristics which make computers better than human beings.
The text in the box below was composed using a word processor. The current cursor position is between the words “is” and “an”.
Describe what happens to the text in the box above when each of the following keyboard keys are pressed.
(a) tab (b) enter (c) home
(a) Tab: Moves the text ahead to the next tab stop or several stops ahead! right) forward.
(b) Enter: Break the line after the word ‘is’ so that the word ‘an’ starts on a new line. Words from “an” forms a new paragraph. (c) Home: Takes the cursor to the beginning of the line. Nothing happens to the text |
Categories
All
Archives
December 2024
|
Can't find what you are looking for? Don't worry, Use the Search Box Below.
|
Primary Resources
College Resources
|
Secondary Resources
|
Contact Us
Manyam Franchise
P.O Box 1189 - 40200 Kisii Tel: 0728 450 424 Tel: 0738 619 279 E-mail - sales@manyamfranchise.com |



















 RSS Feed
RSS Feed

