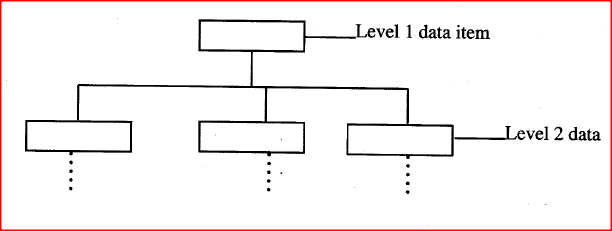
With the aid of a diagram, describe the Hierarchical Database Model.
(b) List three factors that should be considered when developing a database application and give reasons why each should be considered.
(c) (i) Name three types of validation checks during data entry. (ii) Differentiate between primary key and index key RESPONSES
Data items are arranged in a tree like format.
Access is through a single path and all from one single item called the root component. (b) Factors .
0 Comments
What is an information system?
(a) (i) What is an information system?
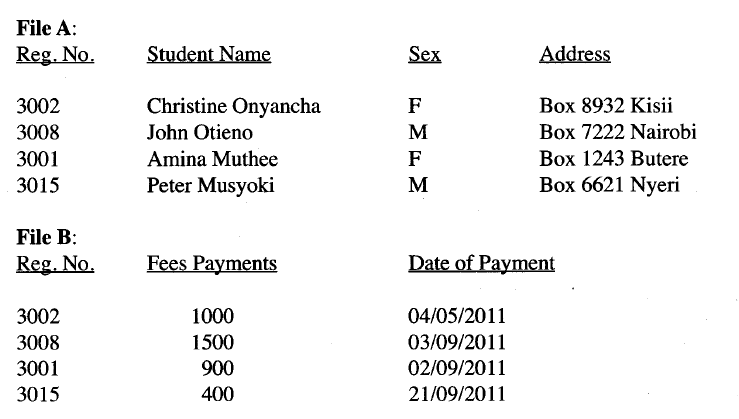
(ii) State two roles of an information system. (b) Describe the following file organisation methods: (i) random file organisation; (ii) sequential file organisation. (c)The following records were extracted from two files that contained student data.
(i) Which of the two files above represents a Transaction file?
(ii) Give a reason for your answer in c(i) above. (iii) Name the other type of file represented above. (d)An airline uses an information system whereby if a passenger at station A books a plane seat,this transaction is immediately shown at stations A and B such that no other passenger can book the same seat. (i) Identify this data processing mode. (ii) State two advantages and two disadvantages of this data processing mode. RESPONSES
(a)(i) Information system is an arrangement of people, data, processes, communication and IT that interact to support problem solving.
(ii) Improve day-to-day operation
(ii) Method of storing or retrieving information that requires the program to start reading at the beginning and continue until it finds the desired data. (c) (i) File B. (ii) Transaction file: It contains data which is regularly added. Has data/fee payment . (iii) Master File: It contains records that do not change regularly like in file A.
(d) (i) Real time processing.
(ii) Advantages
State three techniques used by a network administrator to detect and prevent computer crimes.5/1/2021 State three techniques used by a network administrator to detect and prevent computer crimes.
(b) A company in town wishes to link its offices together. The linking may be through wireless or fibre optic network media.
(i) State two benefits that the company would gain from the use of metropolitan area network (MAN). (ii) State three advantages of using wireless over fibre optic network media. (iii) State two limitations of wireless communication. (iv) State two transmission media used in wireless transmission. (c) State three ways in which computer virus infection can be prevented other than through restricting the usage of removable storage media. RESPONSES
(a) Audit trail
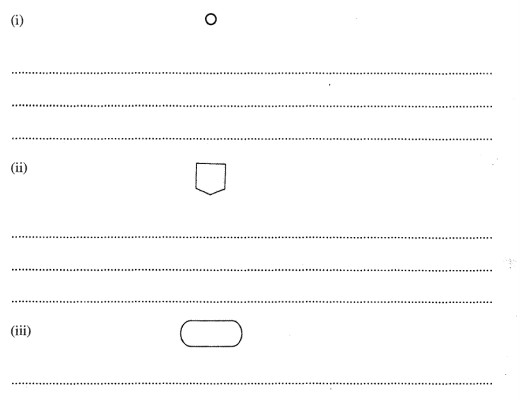
State the use of each of the following flowchart symbols.
(a) Convert each of the following binary numbers to decimal equivalent given that the left most digit is a sign bit.
(î) 0 0 1 0 1 1 0 1 (ii) 1 1 0 0 1 0 0 1 (b) Convert the decimal number 0.42 to 6 bit binary notation. (c) Using two’s complement, subtract 1110 from 810 leaving your answer in binary notation. (d) Perform the following binary operation. 11001 + 1101-101 RESPONSESState the use of each of the following flowchart symbols.
(b)Below is an algorithm that is used to compute the values of R, S and T.
From the algorithm, determine the output if the input value of N is:
(i) 7; (ii) 10. (c) Draw a flowchart for the algorithm in Question 16 (b). RESPONSES
(a) (i) An entry from, or an exit to another part of the program flowchart that is within the same page.
It is an on page connector. (ii) A connector used instead of the connector symbol to designate entry to or exit from a page. It is an off page connector (iii) The beginning and/or end in a program. To start and/or stop/terminate in a program. What is meant by disk defragmentation?
(b) State the purpose of disk defragmentation.
State two roles of a programmer in system development life cycle.
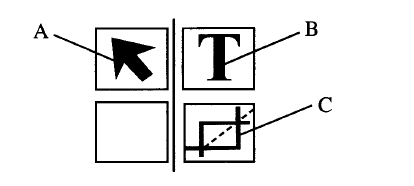
The figure below is a toolbar for a DTP package.State the functions of the tools labelled A, B and C.
A: Selection tool - used for selecting/choosing/highlighting objects on the work area.
B: Text tool - used for enabling typing/editing or insertion of text. C: Cropping tool - used for trimming graphics. State the stage of system development life cycle in which each of the following activities take place:(a) determination of the cost-effectiveness of a system;
(b) interviews;
(c) replacement of an old system with a new one.
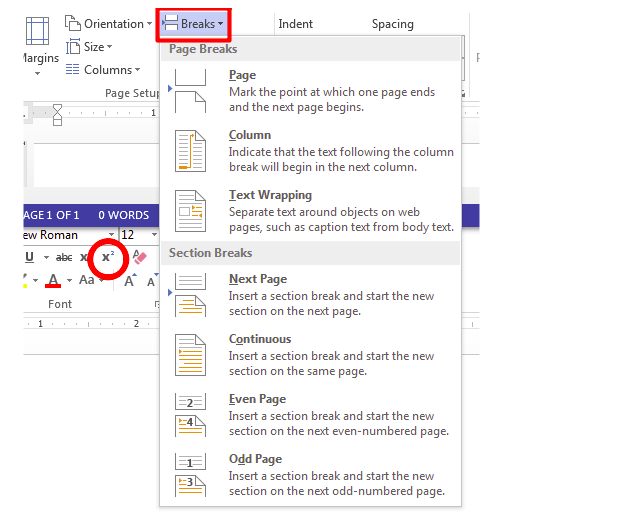
With reference to word processing, describe the term:superscript; and section breaks.(a) superscript;
(b) section breaks.
State two: functions of an email software; protocols used in sending and receiving of emails.5/1/2021 State two: functions of an email software;protocols used in sending and receiving of emails.(a) functions of an email software;
Facilitates mail creation.
(b) protocols used in sending and receiving of emails.
Differentiate between relative cell referencing and absolute cell referencing.
A student saved a document in a diskette. Later on, the student found that the diskette could not open arid therefore the work got lost.Give three precautions the student should have taken to ensure the work was not lost.
Name three types of graphics used in a word processor.
When purchasing a computer, the clock speed, RAM size, Hard disk size and monitor size are often quoted. State the unit for measuring:(a) Clock speed; .
|
Categories
All
Archives
December 2024
|
Can't find what you are looking for? Don't worry, Use the Search Box Below.
|
Primary Resources
College Resources
|
Secondary Resources
|
Contact Us
Manyam Franchise
P.O Box 1189 - 40200 Kisii Tel: 0728 450 424 Tel: 0738 619 279 E-mail - sales@manyamfranchise.com |

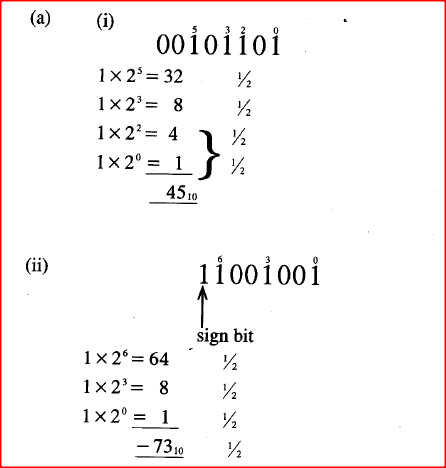











 RSS Feed
RSS Feed

