Explain two ways in which the use of internet could make reporting of corruption easier
(b) Explain two circumstances under which the use of wireless communication would be preferred in data communication.
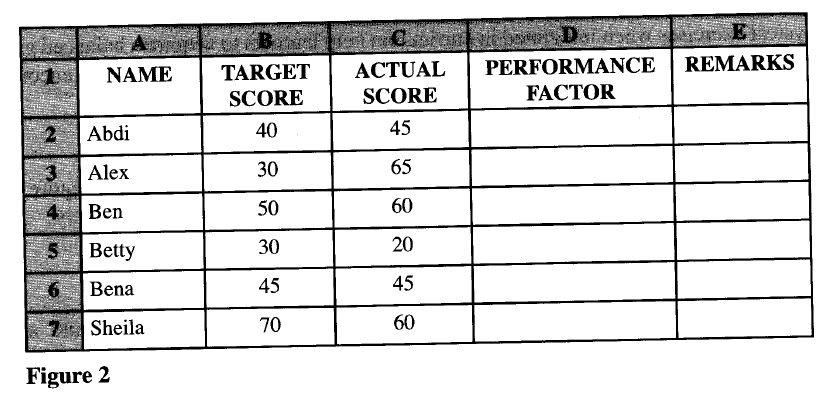
(c) Figure 2 is an extract of a spreadsheet showing what the students had targeted to score and the actual score in a computer remedial class.
A performance factor is obtained by subtracting the target score from the actual score and dividing the difference by the target score.
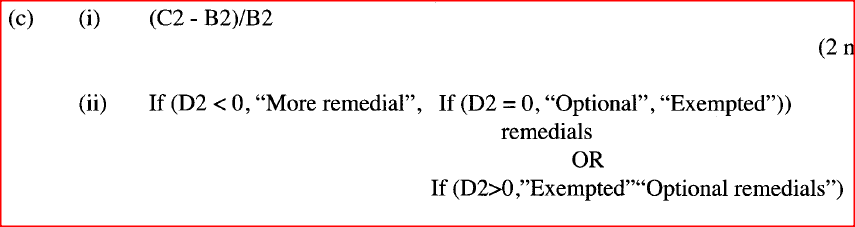
Write a formula that uses cell references only that would be entered in cell: (i) D2 to compute the performance factor. (ii) E2 to display the statement ‘more remedials’ if the performance factor is less than zero, ‘exempted’ if the factor is greater than zero and ‘optional remedials’ if otherwise. (iii) D8 to display the best performance factor.
RESPONSES
(a) Ways ¡n which internet makes reporting of corruption easier.
0 Comments
List two techniques of acquiring electronic images to be used in a desktop publishing program.10/1/2021 List two techniques of acquiring electronic images to be used in a desktop publishing program.
(ii) Describe two layout guides in a desktop publishing program (DTP) that assist a user to place an object in a preferred position.
(b) Explain three ways of ensuring that data submitted for processing is accurate. (c)An engineering company requires a computer system to design roads and bridges. Explain one suitable choice for: (i) output device; (ii) software.
RESPONSES
(a) (i) Ways of acquiring images in DTP:
(ii) A CAD software because it facilitates in the design of engineering drawings. State three functions of networking operating systems other than providing network security.10/1/2021 State three functions of networking operating systems other than providing network security.
(b) Explain three ways in which an operating system provides data security in a computer system.
(c) Explain three circumstances under which observation method may be preferred during data collection.
(a) Functions of network operating systems
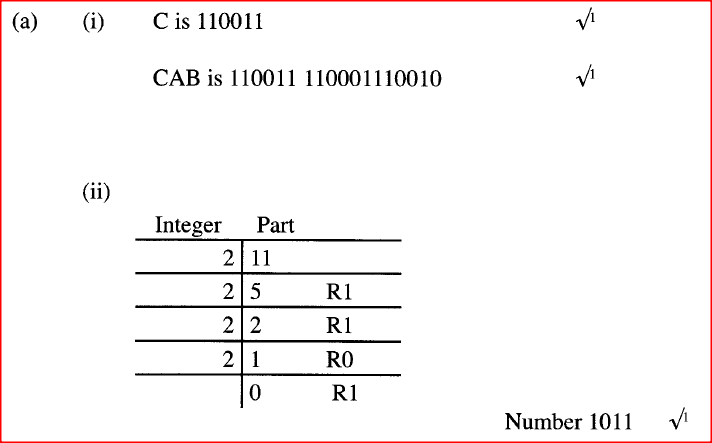
In the BCD number coding scheme, letter A is represented by 110001 and letter B by 110010. Determine how the word CAB is coded in BCD.
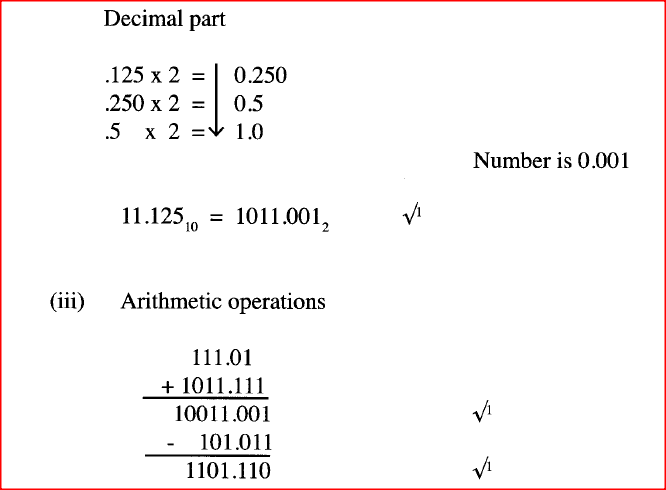
(ii) Convert the decimal number 11.125 to its binary number system equivalent.
(iii) Perform the binary arithmetic: 111.01 + 1011.111 — 101.011 and convert the answer to decimal notation. (b) Explain the importance of each of the following in word processing: (i) tab stops; (ii) section breaks. (c) State three documents that are used during mail merging in word processing.
ANSWERS
(b) Importance of tab stops and section break
List four web programming languages.
State four ways in which a programmer can make program code easy to fol1ow
Using modules or short blocks of program/functions/procedures;
Making internal documentation / comments; Using meaningful variable names and user words in the program; Using indent to represent nested statement: Using blank lines to separate blocks of code statement; Test formatting of reserved words e.g. bolding Draw a program flowchart to represent the following pseudocode.
ANSWER
Distinguish between a systems administrator and a database administrator as used in computers.10/1/2021 Distinguish between a systems administrator and a database administrator as used in computers.
Distinguish between systems administrator and database administrator
Explain two uses of a system documentation in system development.
Uses of system documentation
State three reasons why it is important to define datatypes of fields in a database correctly.8/1/2021 State three reasons why it is important to define datatypes of fields in a database correctly.
Reasons for defining datatypes in databases
State two advantages of making payments through a mobile phone.
Advantages of mobile phone in payments
A computer technician found it necessary to disable a firewall when working on a computer system. State two reasons that may have necessitated disabling of the firewall.
When firewall is disabled
State three circumstances under which voice input would be preferred over other methods of data capture.
Circumstance for voice input
List four factors to be considered when acquiring a printer.
Factors to consider when acquiring a printer
State three benefits of using optical magnetic reader to register candidates for an examination.8/1/2021 State three benefits of using optical magnetic reader to register candidates for an examination.
Benefits of using OMR
State three possible causes of fire outbreak in a computer laboratory.
Sources of fire in a computer laboratory
Distinguish between an assembler and an interpreter as used in programming.
Write the acronym MODEM in full.
Explain the purpose of a modem when connecting to the internet.
State two advantages of using portable computers.
Advantages of portable computers
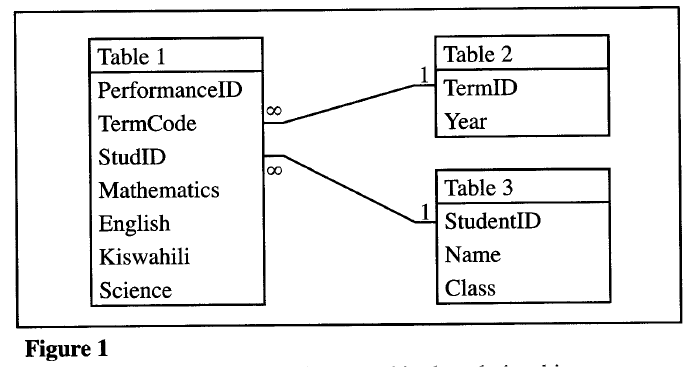
Figure 1 shows relationships between tables in a database.
Identify two primary and two foreign keys used in the relationship.
Primary keys
List six file manipulation activities that may be carried out using an operating system.
File manipulation activities- creation of files/folders
State two circumstances under which warm booting of a computer may be necessary.
Reasons for warm booting a computer
|
Categories
All
Archives
December 2024
|
Can't find what you are looking for? Don't worry, Use the Search Box Below.
|
Primary Resources
College Resources
|
Secondary Resources
|
Contact Us
Manyam Franchise
P.O Box 1189 - 40200 Kisii Tel: 0728 450 424 Tel: 0738 619 279 E-mail - sales@manyamfranchise.com |


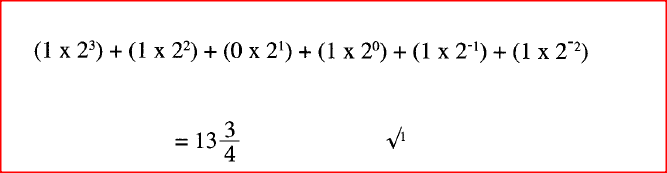














 RSS Feed
RSS Feed

