Explain three ways in which an operating system provides data security in a computer system14/1/2021 Explain three ways in which an operating system provides data security in a computer system
Access control:
(b)State two instances where observation is not a viable method of gathering data during system analysis stage.
I. repeater
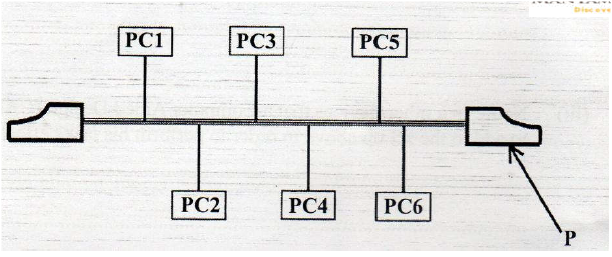
I. Identify the component labelled P.
0 Comments
Explain two health issues that could arise from the use of unsuitable computer desk.
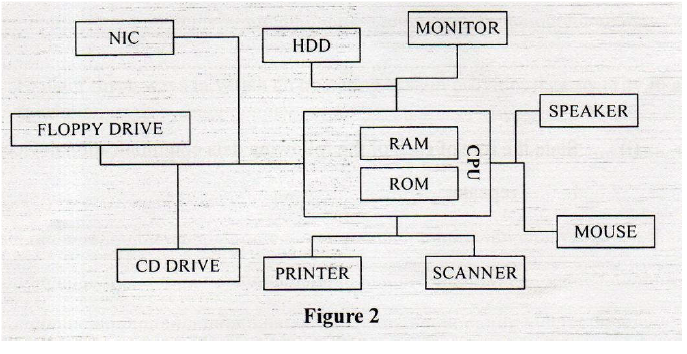
(i)Name two devices that may be used for storing data for a long duration.
Explain two health issues that could arise from the use of unsuitable computer desk.
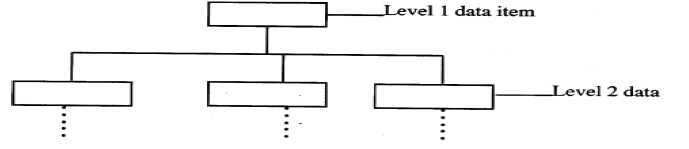
Determine how the number 0.3125 base 10 would be represented. With the aid of a diagram, describe the Hierarchical Database Model.
Data items are arranged in a tree like format.
Factors
(c) (i) Name three types of validation checks during data entry in data processing.
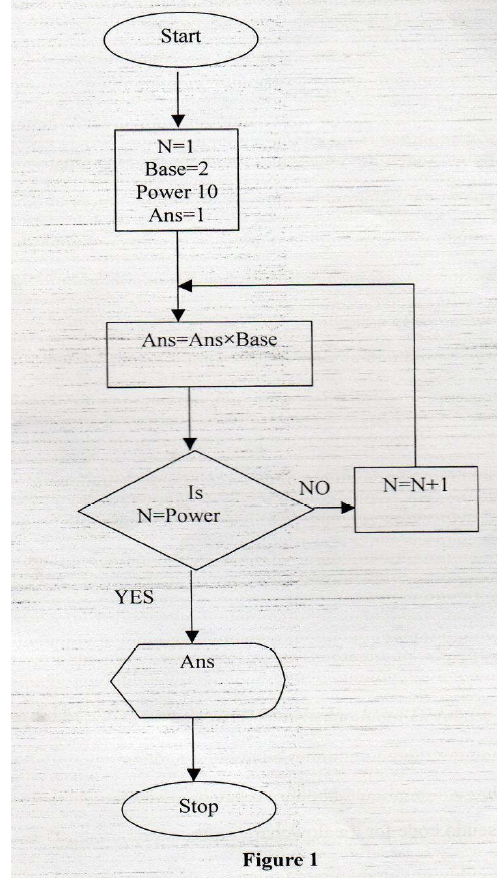
Figure 1 shows a flowchart. Use it to answer the questions that follow.
(a) Interpret the flowchart.
(b) Write a pseudo code for the flowchart. A water company sends out clerks to read meters. The data collected by the clerks is then fed into the computer and then all bills are printed at the same time.
(a)State two advantages of this approach;
The C directory of a computer has folders named Form 1, Form 2,Form 3 and Form 4. Each class has students' folders named according to their admission number. The students created their own folder for subjects they are studying based on the table shown below:
(a) A form four student intends to create a folder named proj to store project documents.
State the path for the project folder.
(i) work is not lost in case the hard disk fails;
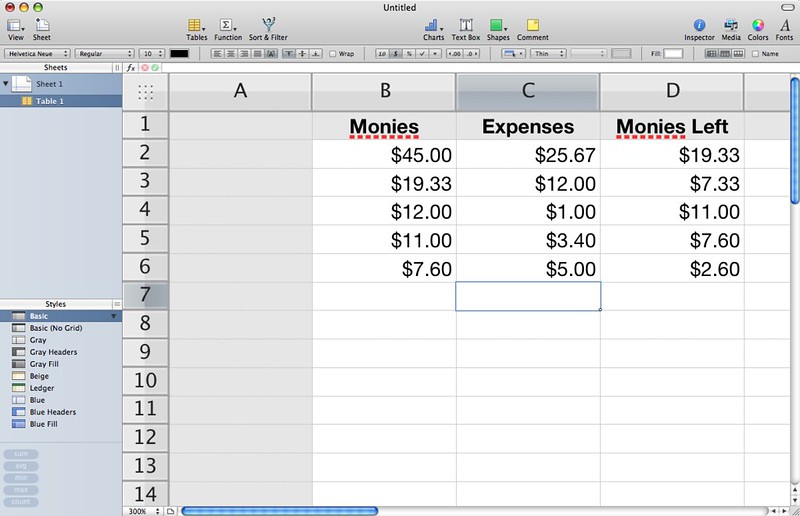
Distinguish between a formula and a function as used in spreadsheets.
List two career opportunities directly associated with computer networking.
Explain why an intranet is a more secure way to share files within an organisation compared to the Internet.
Students of a school intend to elect their school captain by secret ballot. State three ways in which computers can be used to improve the election process.
Headache, back and neck pain may result from the use of computers.
State how each of them can be minimised.
Headache
An organisation intends to replace an existing system by carrying out the process in stages.12/1/2021 An organisation intends to replace an existing system by carrying out the process in stages.
(a) Name this implementation strategy;
Technical feasibility:
State the functions of each of the following keys on the computer keyboard:
(a) backspace;
Convert each of the following binary numbers to decimal equivalent given that the left most digit is a sign bit:
(a) 00101101
(b) 11001001 State two ways in which software errors can be prevented in program development.
Explain two ways in which the use of Internet could make reporting of corruption easier.
Interactiveness:
Pesa Tele Company has offices in Nairobi and Kampala connected in a network. The management is convinced that someone is illegally gaining access to the data in their computers. State three ways in which the company can overcome this problem.
State the meaning of the term disk defragmentation as used in computers.
(a) generating receipts where carbon copies are required;
(b)an architectural drawing where precision is required; (c) producing document output for a visually impaired person.
(a)Carbon copies - impact printers e.g. dot matrix.
(b)Architectural design - plotter (c)Visual impairment - speakers/brailles State the meaning of the term disk defragmentation as used in computers.
State the purpose of disk defragmentation.
|
Categories
All
Archives
December 2024
|
Can't find what you are looking for? Don't worry, Use the Search Box Below.
|
Primary Resources
College Resources
|
Secondary Resources
|
Contact Us
Manyam Franchise
P.O Box 1189 - 40200 Kisii Tel: 0728 450 424 Tel: 0738 619 279 E-mail - sales@manyamfranchise.com |








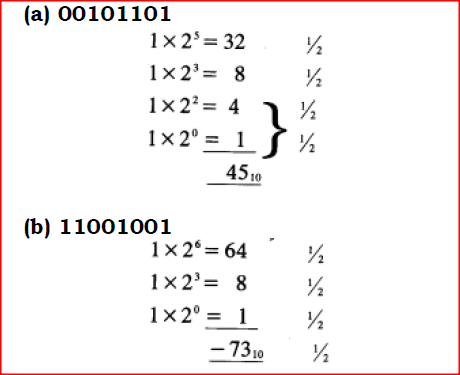





 RSS Feed
RSS Feed

