|
Difference between data privacy and data integrity as used in computing
0 Comments
Explain the meaning of each of the following with reference to computer crime:
State two ways in which users in an organization can be a security threat to data in an information system.
Give four general rules that must be observed to keep within the law when working with data and information
List four ways in which data integrity can be compromised
State the meaning of computer malwareA malicious program designed to harm or disrupt the normal functioning of a computer system e.g. clogging computer memory, unjustified background programs, replicating files etc.
List four signs of a computer system invaded by a virus
John is a first-year student at JKUAT. He is expected to login his student portal to access online assignments. Mention three ways in which he would prevent virus from infecting his computer.
Explain the following terms. (2mks)(a) Computer fraud
use of computer to conceal information or cheat other people with the intention of gaining money or information
(b) Alteration
the legal charging of data or information with the intention of misinforming authorized users or gaining
CHARACTERISTICS OF A COMPUTER INFECTED WITH A VIRUS
State two ways in which one can create a password which cannot be easily accessed by hackers.15/1/2021 State two ways in which one can create a password which cannot be easily accessed by hackers.
Password which cannot be hacked.
Explain three ways in which an operating system provides data security in a computer system14/1/2021 Explain three ways in which an operating system provides data security in a computer system
Access control:
(b)State two instances where observation is not a viable method of gathering data during system analysis stage.
I. repeater
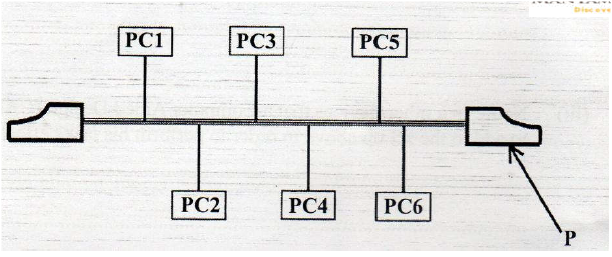
I. Identify the component labelled P.
Pesa Tele Company has offices in Nairobi and Kampala connected in a network. The management is convinced that someone is illegally gaining access to the data in their computers. State three ways in which the company can overcome this problem.
A computer technician found it necessary to disable a firewall when working on a computer system. State two reasons that may have necessitated disabling of the firewall.
When firewall is disabled
State two ways in which hardware failure is a threat to data security.
Peter has installed internet in his home computer in order to use it for browsing. State three ways in which he would prevent viruses from infecting the computer. (3 marks)
A worker is unable to travel to the office but may still be able to do the office work through telecommuting.
(a) Explain why the worker may use each of the following:
(i) email; (ii) fax; (iii) digital camera; (iv) firewall. (b) The worker needs to make regular backups of documents sent to the office. State three reasons for this. (c) Explain two benefits that the employer will get by allowing this worker to do the office work through telecommuting.
RESPONSES
(a) E-mail: - used to send and receive electronic documents to/from the office.
Receive instructions from the supervisor or co-workers. Fax: - Used to send documents which are in non-electronic format Digital camera - Used to capture images in picture form/video conferencing. Firewall - Used to prevent intrusion to the home computer because telecommuting involves connection to the internet. (b) Communication systems may fail/communication channel may fail.
State three techniques used by a network administrator to detect and prevent computer crimes.5/1/2021 State three techniques used by a network administrator to detect and prevent computer crimes.
(b) A company in town wishes to link its offices together. The linking may be through wireless or fibre optic network media.
(i) State two benefits that the company would gain from the use of metropolitan area network (MAN). (ii) State three advantages of using wireless over fibre optic network media. (iii) State two limitations of wireless communication. (iv) State two transmission media used in wireless transmission. (c) State three ways in which computer virus infection can be prevented other than through restricting the usage of removable storage media. RESPONSES
(a) Audit trail
A student saved a document in a diskette. Later on, the student found that the diskette could not open arid therefore the work got lost.Give three precautions the student should have taken to ensure the work was not lost.
One way in which an organisation enforces security of its computer systems is by restricting the use of removable media such as floppy disks and flash memories. Give two reasons for this.
Pesa Mingi company has offices in Nairobi and Kampala connected in a network. The management is convinced that someone is illegally gaining access to the data in their computers. State three ways in which the company can overcome this problem.
State two measures that can be put in place to control piracy of software.
Explain how data in a computer system is secured using:
(i) password;
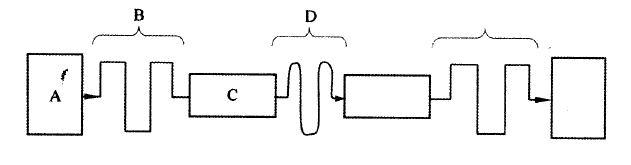
(ii) user access level. (b) State three characteristics of a suitable password. (c) State two characteristics of a computer that is infected by computer viruses. (d)(i) The figure below shows how data is transmitted through a public telephone line.
Name A, B, C and D.
(ii) State two advantages of using fibre optic cables over satellite in data communication.
(a) (i) Password
Copyright laws are laws granting authors the exclusive privilege to produce, distribute, perform or display their creative works. It is a legal framework for protecting the works such as book publishing, motion-picture production and recording. State two challenges that are posed to these laws by ICT’.
|
Categories
All
Archives
December 2024
|
Can't find what you are looking for? Don't worry, Use the Search Box Below.
|
Primary Resources
College Resources
|
Secondary Resources
|
Contact Us
Manyam Franchise
P.O Box 1189 - 40200 Kisii Tel: 0728 450 424 Tel: 0738 619 279 E-mail - sales@manyamfranchise.com |















 RSS Feed
RSS Feed

