Give two reasons why the use of finger prints and voice input can be used as reliable forms of security in computer systems.
They cannot be:
0 Comments
Explain why an intranet is a more secure way to share files within an organisation compared to the internet.
Give a reason for each of the following(a)Changing a password regularly
(b)Typing and re- typing a new password when changing it
Distinguish between the following pairs of terms
(i) Data verification and data validation
Data Validation
State two ways in which each of the following can be prevented: software errors; and computer fraud.31/12/2020 State two ways in which each of the following can be prevented: software errors; and computer fraud.
(a) software errors
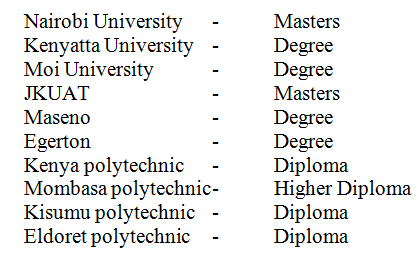
(a) Identify three public Universities and three National polytechnics in Kenya where further computer training is offered, In case state the highest level of qualification that can be acquired in computer training.You have been asked to change your computer password. State a precaution you need to take in order to avoid each of the following: a) Forgetting the password
b) Hacking
Distinguish between the following sets of terms as used in spreadsheets. Worksheet and workbook, Filtering and sorting
b) A student’ database comprises of students’ details table and fees received table as shown below:
Students’ details table
i) State the primary key field for each table.
ii) State the field, which should serve as the linking field for the two tables. c) Describe the following terms with respect to computer security: i) Logic bombs ii) Physical security iii) Tapping d) List three functions of antivirus software.
(i) Log files
(i)State the primary key field for each table.
c) Describe the following terms with respect to computer security: i)Logic bombs A computer virus that is activated after a series of event/commands/date ii) Physical security Threats that threaten the physical nature of computer equipment e.g. Fire, Lightening water, building access etc iii) Tapping.
A firm intends to purchase new software. List three items that should accompany the software26/12/2020 (a) A firm intends to purchase new software. List three items that should accompany the software (3mks)
(a) What are computer viruses?
A computer program designed specifically to damage other programs or cause irregular behaviour.
(b)
|
Categories
All
Archives
December 2024
|
Can't find what you are looking for? Don't worry, Use the Search Box Below.
|
Primary Resources
College Resources
|
Secondary Resources
|
Contact Us
Manyam Franchise
P.O Box 1189 - 40200 Kisii Tel: 0728 450 424 Tel: 0738 619 279 E-mail - sales@manyamfranchise.com |











 RSS Feed
RSS Feed

